Automated BitLocker Encryption Deployment with Microsoft Intune
The blog outlines key prerequisites for deploying BitLocker at scale using Intune, focusing on compatibility, security, and automation. It emphasizes the need for Windows 10/11 with TPM 1.2+ (preferably 2.0), UEFI BIOS, and Azure AD or Hybrid Join for seamless key escrow. Silent encryption requires specific disk partitioning and no third-party encryption tools. Role-based access and network connectivity to Azure AD are also essential for successful implementation and recovery key management.
AZURE
Abhishek Gupta
9/3/202511 min read


In today’s security-conscious enterprise landscape, protecting sensitive data on end-user devices is non-negotiable. Full disk encryption with BitLocker has become a default standard for securing Windows endpoints, especially laptops which are more prone to loss or theft. However, deploying and managing BitLocker across a fleet of laptops in a modern organization demands a streamlined, scalable, and auditable process. Manual enablement is not only inefficient, but also inconsistent, error-prone, and difficult to monitor at scale. Automated solutions are, therefore, vital for compliance and efficiency.
Microsoft Intune, as part of Microsoft Endpoint Manager, offers centralized management and automation capabilities that can greatly simplify the deployment and ongoing management of BitLocker encryption, including policy control, reporting, recovery key rotation, and role-based access. This guide delivers a step-by-step strategy for automating BitLocker using Intune, highlights best practices, addresses role delegation and monitoring, and explores alternative automation routes when Intune is absent. The focus is both practical and strategic, reflecting the latest web-sourced best practices as of September 2025.
1. Understanding BitLocker and Its Enterprise Deployment Imperatives
BitLocker is Microsoft’s built-in full disk encryption technology for Windows devices. It provides strong GPC-compliant protection for data at rest, using the system's Trusted Platform Module (TPM) and recovery keys. When integrated into modern deployment frameworks, BitLocker enables organizations to:
Secure endpoints automatically at scale
Enforce compliance mandates (GDPR, HIPAA, PCI DSS, etc.)
Streamline remote key management and recovery
Reduce data loss impact from lost or stolen devices
Integrate with Azure AD (now Microsoft Entra ID) for seamless cloud-based recovery management
The paramount objective for IT is to roll out BitLocker so that it operates transparently to end users, while affording the organization robust control and audit capabilities.
2. BitLocker Management with Microsoft Intune
Intune, Microsoft’s cloud-native endpoint management solution, provides two main configuration mechanisms for BitLocker:
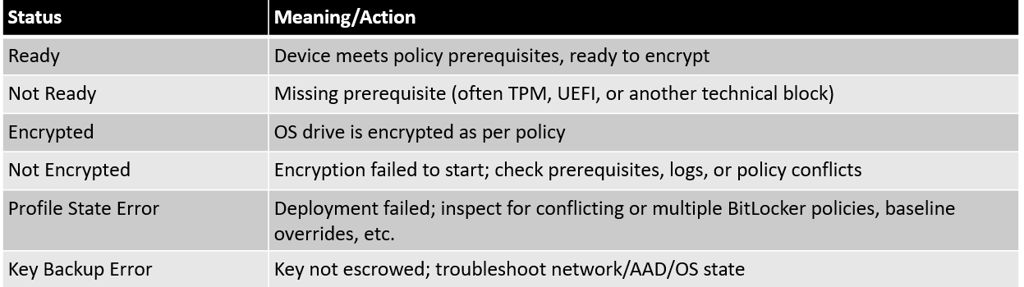
Endpoint Security Disk Encryption Policy (modern, recommended)
Device Configuration Policy (Endpoint Protection Template) (older, still supported)
Both approaches ultimately leverage the BitLocker Configuration Service Provider (CSP) and MDM policies to enforce encryption on target Windows 10/11 devices—facilitating silent, unattended deployment.
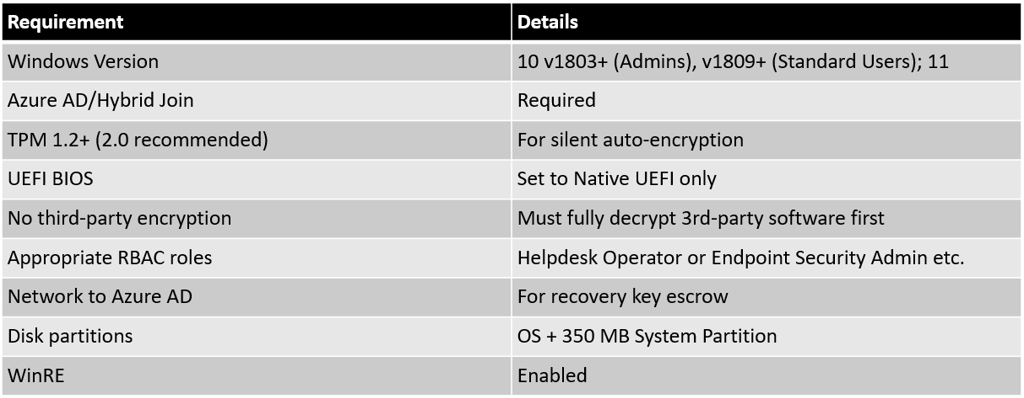
2.1. Prerequisites for BitLocker Deployment via Intune
Before implementing BitLocker through Intune, ensure the following technical and organizational prerequisites are met:
Licensing: Active Microsoft Intune (Microsoft Endpoint Manager) license for administrators and targeted user/devices.
Device Type: Devices must run Windows 10 (version 1803/1809 or later) or Windows 11.
AAD Join Status: Devices must be joined to Azure AD (now Microsoft Entra ID) or hybrid joined (on-premises AD with Azure AD registration).
TPM Requirements: Each device requires a minimum of TPM 1.2 (TPM 2.0 recommended; TPM is essential for silent, userless encryption).
BIOS/UEFI: Native UEFI firmware mode is required; Secure Boot is optional, but recommended for improved security.
No Third-Party Encryption: Devices must not be encrypted with any third-party full-disk encryption software (e.g., McAfee, Sophos, Dell). A full decryption and removal of previous encryption apps is essential before BitLocker can be managed by Intune.
Intune Role-Based Access Control (RBAC): Administrative accounts must have appropriate RBAC roles in Intune for BitLocker management (details below).
Disk Configuration: OS drive must have at least two partitions: one for the OS (NTFS) and a system partition (FAT32 or NTFS depending on UEFI/BIOS).
Windows Recovery Environment (WinRE): WinRE should be enabled for recovery scenarios.
Device Enrollment: Devices should be enrolled in Intune via Azure AD or Entra ID onboarding processes.
Network and Key Escrow: Network connectivity to escrow BitLocker recovery keys to Azure AD during initial encryption.
Failure to meet any of these requirements may result in failed deployments or devices not fully encrypting as planned.
A comprehensive pre-deployment readiness assessment is strongly recommended to avoid deployment issues, particularly where a mix of device hardware, join types, OS versions, or legacy GPOs exist.
2.2. Intune Role-Based Access Control (RBAC) for BitLocker
Managing BitLocker requires adequate permissions. Intune RBAC allows you to delegate specific BitLocker actions (view, rotate, recover keys, etc.) to appropriate roles. Some built-in Intune roles for BitLocker include:
Help Desk Operator: Can view (and rotate) recovery keys but cannot change policy.
Endpoint Security Administrator: Can create and assign disk encryption policies.
Custom Role: You can create a tailored role with permissions such as microsoft.directory/bitlockerKeys/key/read for BitLocker Recovery Key Reader.
Best Practice: Assign BitLocker key access only to trusted helpdesk or security staff and audit all key retrievals in Azure AD logs.
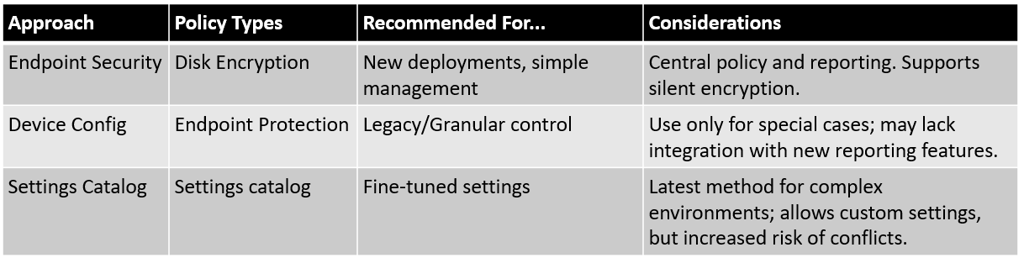
2.3. Methods to Configure and Deploy BitLocker via Intune
There are two principal ways to deploy BitLocker policies in Intune:
2.3.1. Modern Method: Endpoint Security → Disk Encryption Policy [Recommended]
Advantages: Centralized, updated experience; best reporting and client-driven rotation support; easier to maintain.
Access from Intune Admin Center: Endpoint Security → Disk encryption → Create Policy
Choose Platform: Windows 10 and later
Choose Profile: BitLocker
Configure base settings, OS drive, fixed drive, and removable drive settings as per the latest guidance.
2.3.2. Legacy Method: Device Configuration → Templates → Endpoint Protection (BitLocker)
Advantages: More granular settings (if required); supports some older use cases.
Not the preferred pathway, but useful if your tenant has legacy deployments.
Accessible via Devices → Configuration profiles → Create profile → Templates → Endpoint protection → configure Windows Encryption.
On Scope Tags Tab: Apply any administrative scope filters as needed.
On Assignments Tab:
Target to appropriate device groups (for 100 laptops, select dynamic/static groups or pilot sets initially).
Avoid assigning multiple overlapping BitLocker policies—this is a common source of policy conflict.
Review & Create:
Double-check settings, then click Create.
3.2. Notes for Advanced/Settings Catalog Deployments
BitLocker settings are also available in Settings Catalog for fine-grained policies.
Avoid using both Endpoint Security and Device Configuration profiles for BitLocker on the same devices (conflicts occur).
Step 4: Assign and Deploy the Policy
Assign target groups (e.g., “All Corporate Laptops,” “Laptop_Sales”).
Pilot group deployment is highly recommended for initial testing.
Once confirmed, expand assignment to all 100 (or more) laptops.
Avoid deploying BitLocker policies as user-targeted policies; use device-based assignments for consistency.
Step 5: Sync Devices and Trigger Policy Application
Intune delivers policies at next device check-in (typically every 8 hours).
You can instruct users to “Sync” from Settings > Accounts > Access Work or School > Info > Sync for faster policy application.
For bulk triggers, use PowerShell to remote-sync devices via IntuneManagementExtension or reboot.
BitLocker encryption happens automatically/silently as long as prerequisites are met.
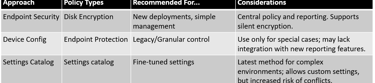
Step 6: Monitor BitLocker Encryption Status and Compliance
Intune provides built-in encryption reports to monitor status, compliance, and troubleshoot issues.
To monitor:
Navigate to: Devices → Monitor → Encryption Report or Device Encryption Status
Fields include:
Device name, OS/version, TPM version, encryption readiness, encryption status, user principal name
Drill into any device for detailed status
Profile State Summary: Shows deployment and error state (e.g., “Compliant,” “Error”)
Export Reports: Optionally, export status as CSV for compliance checks or audits.
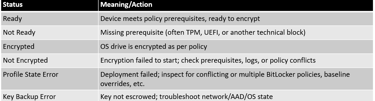
Common BitLocker Monitor Statuses:
3. Step-by-Step Guide: Automated BitLocker Deployment Using Intune
The following workflow ensures both silent (no user prompt) and automatic BitLocker enablement, with recovery keys escrowed in Azure AD and robust monitoring throughout.
Step 1: Prepare Devices and Tenant
Verify the following:
All endpoints are running supported Windows 10/11 editions.
TPM is enabled in BIOS/UEFI (ideally version 2.0).
Devices are Azure AD-joined or Hybrid-joined.
Network connectivity to Microsoft Intune and Azure AD is functional.
Existing third-party encryption (e.g., McAfee, Sophos) has been fully decrypted and software uninstalled.
Windows Recovery Environment (WinRE) is enabled (can be checked with reagentc /info).
Disk partitioning (system and OS) is correct (see prerequisites).
If needed, update TPM firmware, BIOS, or take advantage of Intune’s BIOS configuration profile options for Dell and select OEMs to automate BIOS changes (e.g., activate TPM, switch to UEFI mode).
Step 2: Assign RBAC Roles for BitLocker Management
Assign the following Intune roles to administrators and helpdesk/support staff:
Endpoint Security Administrator: Policy configuration and deployment
Help Desk Operator: Recovery key access and rotation
Custom BitLocker Recovery Key Reader: For highly granular access, assign microsoft.directory/bitlockerKeys/key/read only.
Note: All recovery key access is auditable in Entra ID / Azure AD audit logs.
Step 3: Create and Configure the BitLocker Policy in Intune
3.1. Using Endpoint Security Disk Encryption Policy (Modern Experience)
Go to: Intune Admin Center
Navigate to: Endpoint security → Disk encryption → Create Policy
Select:
Platform: Windows 10 and later
Profile: BitLocker
On Basics Tab:
Name your policy (e.g., “Standard Laptop BitLocker Policy”)
Add description for context and auditability
On Configuration Settings Tab:
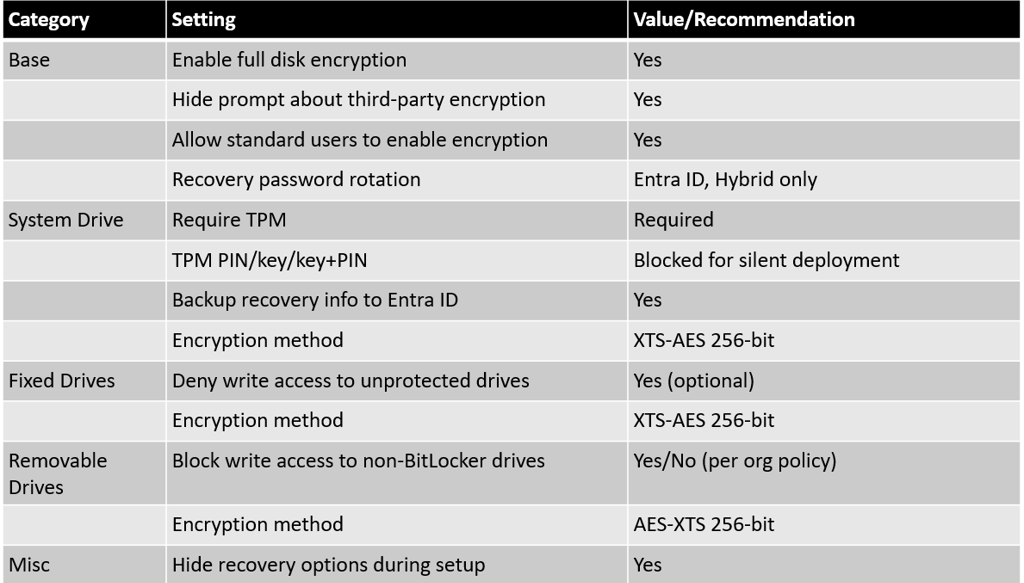
Base Settings:
Enable full disk encryption for OS and fixed data drives: Yes
Hide prompt about third-party encryption: Yes
Allow standard users to enable encryption (Autopilot): Yes
Configure client-driven recovery password rotation: Enable rotation on Entra ID and Hybrid-joined devices
Require Device Encryption = Enabled
Allow Warning for Other Disk Encryption = Disabled
Operating System Drive Settings:
BitLocker system drive policy: Configure
Require TPM: Required
Compatible TPM startup PIN, key, key+PIN: Blocked (Blocking these options is essential for silent enablement. If required, do not use silent deployment.)
Recovery key creation: Required; Backup to Entra ID: Yes; Hide recovery options during BitLocker setup: Yes
Encryption method: XTS-AES 256-bit
Fixed Data Drives:
Fixed drive policy: Configure
Recovery key creation: Required
Backup recovery info to Entra ID: Required
Deny write access to unprotected fixed drives: Yes (optional, for stricter compliance)
Encryption method: XTS-AES 256-bit
Removable Drives (optional):
Removable drive policy: Configure
Block write access to removable drives not protected by BitLocker: No/Not configured (or Yes for high security)
Encryption method: AES 256-bit XTS or AES-CBC 256-bit
Example Table – Endpoint Security Disk Encryption Policy Core Settings:
Tip: Intune may take up to 24 hours to reflect status changes. Manual device “Sync” or forced check-in accelerates reporting turnaround
Step 7: BitLocker Recovery Key Management and Rotation
Azure AD/Entra ID Key Escrow:
Recovery keys are uploaded and tied to each device record.
Access via: Intune admin center → Devices → [Device] → Recovery Keys
BitLocker Key Rotation:
Policies enable automatic (“client-driven”) recovery key rotation after use, reducing the risk of key exposure reuse.
Admin can trigger key rotation remotely via Intune console for any device.
Self-service user recovery is available via Company Portal if allowed; use conditional access and audit controls for security.
Step 8: Ongoing Compliance, Audit, and Self-Service
Audit all recovery key reads: Entra ID logs every access for compliance.
End user self-service: Optionally allow users to retrieve their own recovery keys (offload helpdesk load) in Entra ID / Portal.
Regularly review compliance reports and generate alerting for any devices not encrypted, not reporting, or whose policy state is in error.
4. Troubleshooting Intune BitLocker Deployments: Conflicts and Failures
BitLocker deployment conflicts are common in multi-policy or hybrid environments.
Common Sources of Policy Conflict:
Multiple assignments: Do not assign BitLocker settings from both Device Configuration and Endpoint Security profiles to the same group/device.
Security baselines vs. direct policies: Security baselines may configure (override) BitLocker/TPM settings (e.g., requiring a TPM PIN or key), which blocks silent encryption.
Group Policy vs. Intune settings: On hybrid-joined devices, local GPO wins over MDM unless “MDMWinsOverGP” CSP is configured. Remove or update legacy group policy to avoid drift.
Legacy MBAM or SCCM policies: These may set conflicting key storage/encryption method settings.
Devices not meeting prerequisites: (e.g., missing/disabled TPM, BIOS in legacy mode, old OS version, no system partition, WinRE disabled, etc.)
Diagnostic Steps
Encryption Report Details: Review status and errors in Intune admin center, Device Management logs, or BitLocker event logs.
Event Viewer: Use Windows Event Viewer (Applications and Services Logs > Microsoft > Windows > BitLocker-API) to check for encryption, protector, or backup errors.
manage-bde -status: Use this command to check volume encryption details on troubleshooting endpoints.
Review assignment conflicts: Remove duplicate or conflicting assignments as surfaced in Intune logs or portal.
Resolution of Conflicts
Remove duplicate assignments or baseline policies as needed.
Adjust group membership so each device receives only one BitLocker policy.
For hybrid-joined devices, migrate BitLocker management fully to Intune or stick with GPO—avoid mixing.
For legacy-encrypted devices, backup and rotate keys into Azure AD using PowerShell (BackupToAAD-BitLockerKeyProtector).
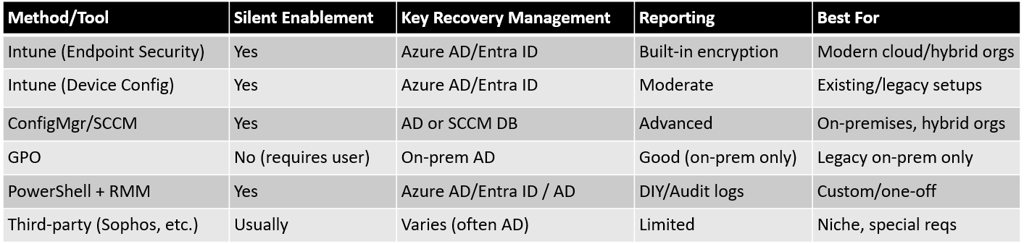
5. PowerShell and Other Automation Approaches (Outside Intune)
If Microsoft Intune is not available or only partial automation is needed, several options exist:
5.1. PowerShell Script Automation
A robust PowerShell script can automate BitLocker enablement, TPM validation, and recovery key backup for existing or newly imaged laptops:
Check for TPM presence and readiness (Get-Tpm)
Check BitLocker installation
Enable BitLocker with TPM protector:
Enable-BitLocker –MountPoint “C:” -TpmProtector
Create and backup recovery key:
BackupToAAD-BitLockerKeyProtector (for Azure AD/Hybrid-joined devices)
Ensure recovery keys reside in Azure/Entra ID or AD
Script can run in test mode or with -force for non-interactive use
Best suited for use with RMM tools, Domain startup scripts, or GPO scheduled tasks.
Sample script and workflow:
See Bytiful.com’s script (2024) for a comprehensive, production-ready example.
Remember to test PowerShell scripts thoroughly and consider local admin or SYSTEM context for full effect.
5.2. Microsoft Configuration Manager (SCCM) and MBAM
Organizations with on-prem SCCM (ConfigMgr) can manage BitLocker directly via:
SCCM Native BitLocker Management (post-2103):
Policies for drive encryption, recovery key storage (in AD or CM database)
Web-based portals for helpdesk/self-service recovery
Robust reporting, compliance, and role-based access.
SCCM/MBAM/Intune co-management possible (pick one platform as “owner” per device to avoid drift/conflict).
Note: Intune is now generally recommended for cloud-first orgs or hybrid environments.
5.3. Group Policy Objects (GPO)
On-premises Active Directory organizations—without Intune—can leverage GPOs for BitLocker:
Full range of BitLocker options exposed under
Computer Configuration > Policies > Administrative Templates > Windows Components > BitLocker Drive EncryptionSupports granular targeting (OUs, security filtering)
Recovers keys to Active Directory
Does not work for remote/roaming/off-domain devices or for cloud-native management.
5.4. Third-Party MDM and Encryption Suites
Alternatives include:
MobileIron, VMware Workspace ONE, JAMF for Mac
Third-party “front-ends” for BitLocker: (e.g., Sophos, Dell/EMC, McAfee, BitTruster, VeraCrypt for open source/offline use) but most only layer on management on top of BitLocker—key storage and recovery options may be inferior to Intune/Azure AD integration.
Standalone Open Source: VeraCrypt, DiskCryptor, etc.—for personal, non-enterprise, or non-Windows scenarios
6. Hybrid Join & BitLocker Recovery in Azure AD and On-Premises AD
For hybrid environments, BitLocker recovery keys can be escrowed to both Azure AD and on-premises AD. Beware of timing issues (e.g., device not fully joined to Azure at encryption time), as this can result in recovery keys only stored in AD, not AAD. PowerShell scripts can migrate keys into Azure for such “legacy” devices.
Key Practices:
Use a PowerShell script to run BackupToAAD-BitLockerKeyProtector post-enrollment to ensure key presence in Entra ID.
Report on all devices without AAD recovery keys and address as needed (see Microsoft Graph API examples for automation at scale).
Self-service key recovery is available both from on-prem AD tools and Entra ID portal, depending on how/where the key is stored.
7. Best Practices and Advanced Configuration
7.1. Silent and Automatic Encryption
Never require a startup PIN/key for silent encryption.
Block startup PIN/Key requirements in policy; only allow TPM booking.
Audit frequently for drift if security baselines or vendor images might override desired settings.
Always pilot on a small set of hardware variations (including virtual, modern standby, and legacy BIOS) first.
7.2. Secure BIOS and TPM
Use Intune BIOS policies for supported models (e.g., Dell) to automate UEFI/TPM enablement before deploying BitLocker. Misconfigured BIOS can silently halt encryption plans.
Ensure BIOS/TPM password management is secure and audited—randomized per device, with central auditing.
7.3. Removable Media Encryption (BitLocker To Go)
Intune can enforce BitLocker for removable drives but cannot enforce auto-encryption or auto-key escrow. Use administrative scripts and Event Log triggers to upload keys to Azure AD for each removable drive encryption event—see SMBtotheCloud for script examples and scheduling tasks.
7.4. Security Baselines
Apply security baselines thoughtfully. Some settings in Microsoft Defender for Endpoint (e.g., require PIN or key for TPM) will conflict and block silent encryption. Always review assigned baselines and remove or align with your intended BitLocker policy.
8. Summary Table—Deployment Pathways and Key Features
9. Recommendations
Automated, silent BitLocker deployment via Microsoft Intune is now the industry standard for Windows devices, offering robust, scalable, auditable, and secure full disk encryption—essential for protecting mobile endpoints such as laptops. By following this structured approach, you can:
Ensure organizational compliance with data protection mandates
Achieve audit- and compliance-friendly recovery key management
Deliver a seamless, zero-impact user experience (no manual intervention required)
Respond rapidly to lost devices or recovery events with key rotation and remote support
Careful attention to prerequisites, single-source-of-truth policy design, and ongoing monitoring are the pillars of sustainable full-disk encryption management. Organizations still reliant on GPO or SCCM/MBAM should plan for migration to Intune for optimal automation and cloud integration.
If Intune is not available, PowerShell automation and/or ConfigMgr remain viable, but require manual maintenance and less slick integration with Azure AD/Entra ID. After initial rollout, regular compliance and reporting checks are advised to ensure ongoing protection across your hardware estate.